The computer system attack suffered by several essential services of the Catalan government with the intention of preventing the first Catalan independence consultation, the so-called Consulta of 9-N, held on November 9th 2014, was perpetrated "from a distance no further than 1,000 kilometres" from Catalonia, according to new information to which ElNacional.cat has had access. That cyberattack, which aimed to paralyse the web portal for the unofficial citizen consultation on independence from Spain, caused the disruption of key administrative areas that had nothing to do with that election day, such as Catalonia's Medical Emergency Service, the electronic pharmacy prescription service, mobility services and the main websites of the Catalan government.
It was not Chinese, Russian, or American
Last week, the newspaper El País reported that an Israeli businessman, Tal Hannan, had been the mastermind of the operation and the following day radio programme El Món a RAC1 added that this type of assignment can only be fulfilled if the client is the government of a state. The fact that the author is an Israeli businessman does not in any way indicate that the physical origin of the computers from which the attack is launched is Israel. At that time, the Catalan government did not yet have its current Cybersecurity Agency and, thus, was unable to formally investigate the geographical origin of the cyberattack after it happened.
The version that Spanish authorities gave to the media was that the origin of the cyber attack was in Russia, China and the United States, because this was indicated by the Internet Protocol (IP) addresses of the "digital cybermissiles" that had struck the information systems of the Generalitat de Catalunya. Despite not having the tools to start the investigation, some government IT officials consulted expert hackers and managers of large telecommunications infrastructures in order to have more data on the origin of this cyberattack. The information obtained was kept secret until today, and ElNacional.cat has had access to it.
The details of the 9-N cyberattack
The attack which took place on the days leading up to the 9-N was an attack as simple to explain as this: "It is as if to paralyse the city of Barcelona, you bring to its entry points a quantity of cars 60,000 times higher than on a normal day. The city will be blocked and no one will be able to enter or leave", sources who were part of the Catalan government at the time explained to this newspaper. In more technical terms, this attack is known as a Distributed Denial of Service Attack (DDoS), that is, one that employs thousands of computers to simultaneously target a single site or a small number of sites. The site in question cannot handle the huge demand, thus it is paralysed and is unable to serve normal users.
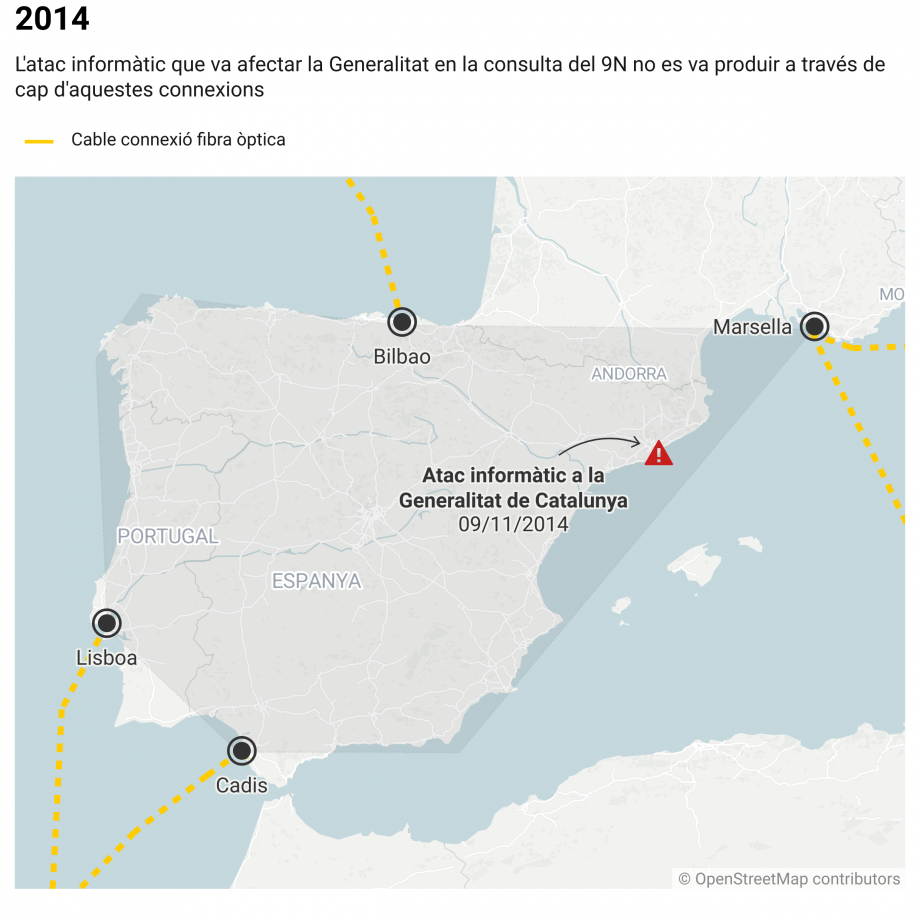
However, as ElNacional.cat has learned, even if the IPs of the computers that carried out the attack had Chinese, Russian or American registrations, their place of origin was not in any of these territories "but at some point no further away from Catalonia than 1,000 kilometres”. The proof of this geographical-adjacent origin, which adds new arguments to suggest the Spanish government's responsibility in the case, must be found in the underwater digital cables that convey information between the Iberian Peninsula and the rest of the world.
Last October, Catalonia obtained its own connection to a submarine cable on one of the main routes on the planet, with its point of landfall being just north-east of Barcelona city, at Les Tres Xemeneies, in Sant Adrià de Besòs. The connection to this cable is the result of years of negotiation between different Catalan governments and the companies responsible for these infrastructures. In fact, the first negotiations took place in 2014, under the government of Artur Mas. It was while they were engaged in negotiations on the cable connections that the Catalan administration suffered this cyberattack and the adminstration's IT security officials asked these international companies if they had detected that huge volume of data passing through their submarine cables in the days before Novermber 9th.
Intercontinental traffic did not increase
It should be recalled that that cyberattack was listed as one of the 10 most significant cyber security incidents in the world in 2014. A full 95% of intercontinental data traffic travels through submarine cables and, thus, to perpetrate a cyberattack of this magnitude, the required digital flows would have passed along the cables that connect the Iberian Peninsula with the American and Asian continents. Yet there is no trace of this. "Not one single bit" entered via the major intercontinental submarine cables that reach Bilbao, Lisbon, Cádiz and Marseille. Thus, if the cyberattack did not enter from outside the Iberian peninsula, "it is quite obvious" that it was executed with infrastructure from a point inside these four vertices and "having previously falsified the IPs (the location-revealing digital addresses) to make people believe they came from far away and thus divert attention".
To provide further confirmation of the authorship of the cyberattack, the Catalan administration's IT managers themselves recommend changing the scope of the investigation: "Just like in The Wire with police pursuing drug traffic, it will be easier to follow the trail of the money paid to Tal Hannan". Of course, they add, that this may not be easy because it could have passed through the Spanish government's so-called "reserved funds", budget items used for security and intelligence purposes and hidden from public scrutiny.

